How ITAD Supports Zero Trust Architecture

As Zero Trust becomes the gold standard for cybersecurity frameworks, many organizations are tightening access controls, segmenting networks, and closely monitoring user behavior. While these strategies are essential, one area is consistently overlooked, and it’s putting enterprise data at risk.
That area is IT asset disposition (ITAD). If your Zero Trust strategy doesn’t extend to how you handle retired hardware, you’re leaving a back door wide open.
Here’s how secure, compliant ITAD strengthens your Zero Trust posture and why it’s time to rethink what “always verify” truly means.
What Is Zero Trust, and Why Doesn’t It Stop at the Firewall?
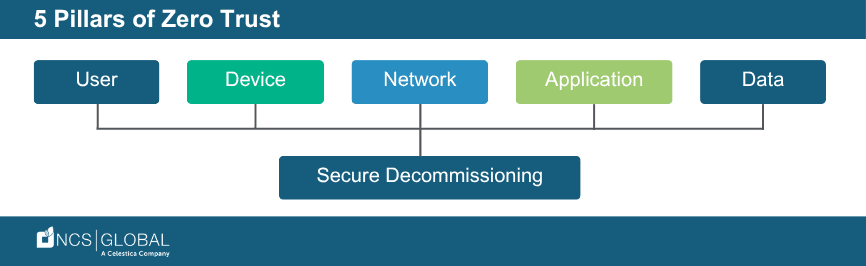
Zero Trust is grounded in a simple principle: never trust, always verify. That means every access request, device, user, and transaction must be authenticated, authorized, and continuously validated.
Despite all the focus on endpoints, applications, and networks, the physical lifecycle of IT assets often gets ignored. Laptops, servers, and drives that are decommissioned may seem like old news, but unless they’re properly erased and tracked, they remain potential sources of data leakage.
Ignoring asset disposition creates a blind spot in an otherwise rigorous security strategy. For Zero Trust to be truly comprehensive, it must include a secure, verifiable end-of-life process for hardware.
The Risk of Unsecured Asset Disposal
Retired IT assets may no longer be connected to your network, but that doesn’t mean they’re harmless. Hard drives can still contain unencrypted or recoverable data, and when those devices aren’t properly wiped or tracked, they become liabilities.
Consider this real-world example: Affinity Health Plan paid over $1.2 million in HIPAA fines after it returned leased photocopiers without erasing the data stored on their hard drives. Those drives contained the protected health information of more than 340,000 individuals. It wasn’t a hack. It was a failure to properly manage asset disposition. In a Zero Trust world, that’s an unacceptable risk.
These kinds of incidents undermine security and erode trust with customers and regulators. In the Zero Trust model, “out of sight” can never mean “out of mind.”

How ITAD Fits Into Zero Trust Security
A well-designed Zero Trust strategy accounts for every interaction, every device, and every transition, including the moment an asset leaves your control.
Secure ITAD services play a crucial role here. NCS Global follows a certified data erasure process based on NIST 800-88 standards, ensuring all sensitive information is permanently destroyed before the asset leaves your site or ours.
We apply a full chain-of-custody protocol to every device, with logging, tagging, and tracking at each step. This creates a transparent, auditable trail that reinforces trust and ensures compliance. Whether your team needs documentation for a cybersecurity audit or evidence for regulatory review, we deliver the data.

NCS Global’s Role in Supporting Zero Trust Initiatives
Supporting Zero Trust requires operational discipline and verifiable control. That’s why our services are purpose-built for enterprises with elevated security expectations.
Our proprietary EcoErase software provides customizable, multi-pass data wiping that can be deployed on- or off-site. For organizations handling particularly sensitive information, we also offer physical destruction services, including degaussing and shredding.
What truly sets us apart is our client portal. With real-time asset tracking, compliance logs, and detailed reports, your team always has access to the full picture, from pickup to final disposition. It’s secure disposal and a seamless extension of your Zero Trust ecosystem.
ITAD and Compliance: SEC, NIST, HIPAA, GDPR, and More
Regulatory pressure is rising across sectors. From the GDPR’s right to erasure to HIPAA’s data destruction mandates, organizations are increasingly expected to prove they’ve secured the full data lifecycle.
At NCS Global, we design our ITAD services to meet or exceed the expectations of these frameworks. Our processes align with NIST, SEC, HIPAA, and GDPR standards, providing confidence that your retired assets won’t become future liabilities.
Because our documentation is audit-ready, your compliance and security teams can work from the same set of trusted reports.

Close the Loop on Zero Trust with NCS Global
Zero Trust isn’t a product. It’s a mindset—a commitment to never assume, always verify.
That commitment doesn’t end with the network. It extends to every stage of the data lifecycle, including the moment an asset is retired. Without secure ITAD, your Zero Trust architecture is incomplete.
Partner with NCS Global to protect your hardware, your data, and your reputation, all the way to the end.