Secure Data Destruction for Remote Teams: What Changed After 2020

Data security has become more complicated in the age of remote and hybrid work.
In a recent Kensington survey of 1,000 senior IT decision makers across the US and EMEA, 93% of organizations reported an increase in security risks due to the shift to flexible and hybrid working models. These risks extend beyond physical device theft to include heightened vulnerabilities in data protection caused, in part, by decentralized work environments.
Remote Work by the Numbers
A majority of U.S. companies now allow remote work, with 26% of employees working exclusively as remote workers, and another 52% working in a hybrid environment that allows for both working remotely and in-office, according to Gallup research.
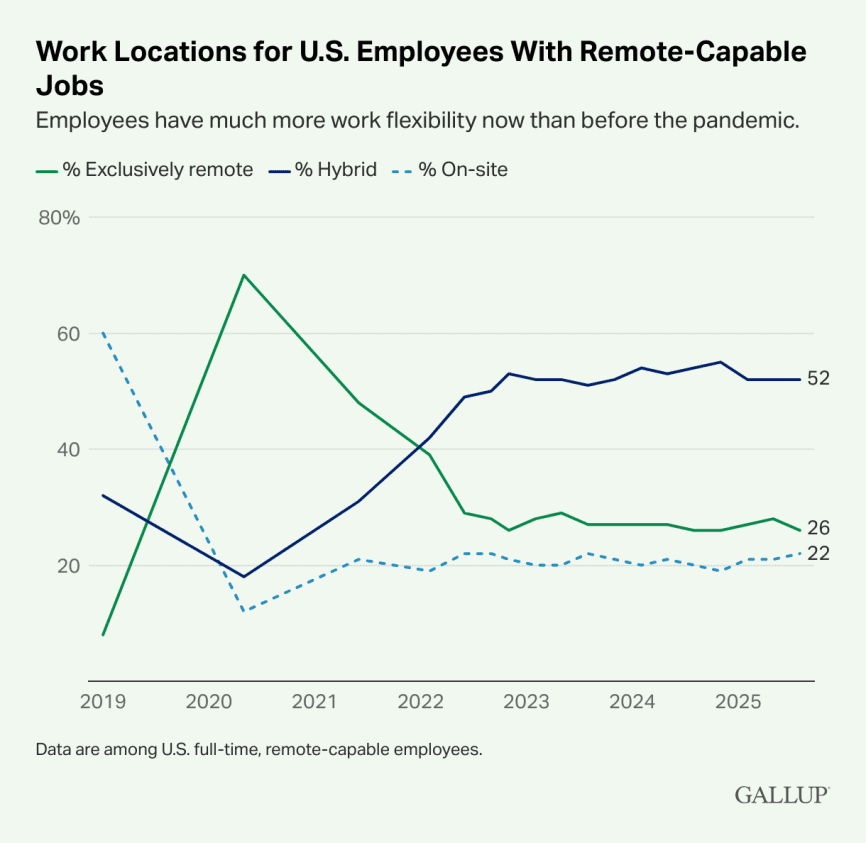
The Shift to Remote Work Created New Risks
When the world went remote in 2020, IT teams were forced to adapt fast. Corporate devices were shipped to employee homes en masse, with little time to plan for how they’d be tracked, retrieved, or securely decommissioned later.
While many companies quickly figured out how to support remote productivity, far fewer developed long-term strategies for managing the full lifecycle of remote assets.
This gap has become a major compliance risk because end-of-life IT asset management in a distributed workforce isn’t just about shipping boxes. It’s about securing sensitive data and proving you did it, at scale.

Here are three key challenges organizations still face:
- Decentralized assets are hard to track. Devices issued to remote employees may never return, especially during offboarding. Without a reliable asset inventory system and enforcement process, these devices become major blind spots.
- Inconsistent decommissioning processes. IT offboarding checklists vary by team, department, or region. Some devices are wiped properly; others are forgotten or left vulnerable to data leaks.
- More complex audits. Whether it’s for GDPR, HIPAA, or internal governance, compliance audits now require visibility into distributed IT assets. Without standardized chain-of-custody documentation and certified data destruction records, proving compliance is difficult.
Without a consistent, secure process in place for managing remote asset disposition, organizations face serious financial, legal, and reputational risks.
Remote Devices Still Need Certified Destruction
It doesn’t matter where a device is located. Data privacy regulations require the same level of care and verification.
Remote work isn’t an exemption from compliance.
Sensitive data must be securely destroyed according to standards like:
- NIST 800-88 Rev. 1: Guidelines for media sanitization that specify how data should be irretrievably erased or physically destroyed.
- DoD 5220.22-M: Former Department of Defense standard requiring multiple-pass overwrites and verification.
- GDPR: Mandates the secure disposal of personal data, with potential fines for noncompliance.
- HIPAA: Requires that Protected Health Information (PHI) be securely destroyed when no longer needed.
Yet many organizations still rely on outdated or ad-hoc practices for remote devices:
- Hoping employees will return laptops (many don’t)
- Trusting remote staff to wipe their own drives (risky and unverifiable)
- Skipping destruction altogether for lower-value assets (a compliance liability)
If you can’t verify it, you can’t prove it.
This is where having a trusted ITAD partner with secure, documented processes becomes essential for compliance and peace of mind.
How NCS Global Delivers Secure Erasure Anywhere
At NCS Global, we recognized early that the future of IT asset disposition would be decentralized.
That’s why we’ve built our services and our proprietary software, EcoErase™, to meet the needs of distributed teams.
Whether your devices are in corporate HQs, home offices, or third-party storage facilities, NCS Global can ensure secure, certified data destruction with full traceability.
Here’s how it works:
- Remote pickup and logistics coordination: Our team schedules secure pickups from remote sites or employee homes, using verified transportation partners and serialized tracking throughout.
- Onsite or offsite erasure with EcoErase™: Devices are either erased at the pickup location (using EcoErase deployed via portable drives or secure connections) or transported to an NCS Global facility for certified destruction.
- Digital certificate issuance: Each device is assigned a unique certificate of destruction or erasure, tied to its serial number, date, and location—essential for audit readiness.
- Chain-of-custody assurance: All steps are documented, logged, and visible through a secure portal, ensuring accountability from start to finish.
NCS Global brings the solution to you, wherever your team works. Because EcoErase is fully compliant with NIST 800-88, HIPAA, and GDPR standards, your data stays protected throughout the process.
Stay Compliant Across a Distributed Workforce
Regulatory scrutiny around data destruction is only increasing, especially for industries like healthcare, financial services, education, and government.
These sectors must meet stringent rules for data privacy, secure disposal, and audit documentation. With devices now spread across multiple locations, that’s easier said than done.
Working with NCS Global means you’ll be able to:
- Meet internal and external audit requirements. With digitally tracked documentation and certificates of destruction, audits become simpler and defensible.
- Support ESG and security reporting. Responsible IT asset disposal is part of a broader sustainability and compliance strategy. Our services align with corporate goals around data security and environmental impact.
- Minimize downtime and disruption. Our logistics-first approach ensures device pickups and sanitization processes don’t interfere with day-to-day operations, even when dealing with hundreds or thousands of assets.
Whether you’re responding to a data privacy inquiry or preparing for an audit, we give you the tools, documentation, and peace of mind you need to protect your business.
Why Secure ITAD Is Now a Strategic Priority
It’s no longer just IT’s problem.
Secure data destruction is now a concern for:
- IT Managers and Asset Managers tracking devices and maintaining inventories
- Compliance Officers verifying proper disposal and regulatory adherence
- CIOs and Risk Teams managing organizational exposure and governance
The truth is, you can’t afford to treat data destruction as an afterthought, especially in a remote or hybrid work environment. Devices get lost. Employees turn over. Regulations tighten.
NCS Global helps you stay ahead by providing scalable, secure, and transparent solutions that fit your new normal.
Ready to Close Your Remote Security Gaps?
The shift to hybrid work changed how IT teams manage risk and left many scrambling to catch up.
With EcoErase, remote logistics, and a fully documented chain of custody, NCS Global makes it easy to implement certified, compliant, and cost-effective data destruction across your distributed workforce. NCS Global brings certified, trackable solutions directly to your team, no matter where they work. Contact us today for secure data destruction.